Blog
New Feature
/ 5 May, 2025Achieving Least Privilege: Unused Entitlement Removal
Unused entitlements are one of the easiest ways for an attacker to move laterally in a target environment.
However, reducing permissions is often very difficult due to availability concerns and the complexity of the permission systems.
This blog post explores how SlashID solves this problem so that customers can automatically resize identity permissions and
achieve least privilege.


New Feature
/ 5 May, 2025Achieving Least Privilege: Unused Entitlement Removal
Unused entitlements are one of the easiest ways for an attacker to move laterally in a target environment.
However, reducing permissions is often very difficult due to availability concerns and the complexity of the permission systems.
This blog post explores how SlashID solves this problem so that customers can automatically resize identity permissions and
achieve least privilege.


Security
/ 18 Jan, 2024Single Sign-On implementation: Safely retrieving the email claim
A number of security issues have been discovered recently caused by the reliance on the email claim when using OpenID Connect (OIDC) for SSO.
In this blog post we'll review some of the major OIDC providers to discuss how to retrieve the claim safely


Security
/ 8 Jan, 2024Single Sign-On implementation: Security Issues and Best Practices
Social logins and OpenID Connect (OIDC) are an extremely effective way to register new users with low friction.
There are many libraries out there that implement OIDC with several providers, however the implementation is very error-prone and can expose an application to account takeover attacks.
In this article, we’ll discuss the common security issues found in OAuth 2.0/OIDC login flows and best practices on how to avoid them.


New Feature
/ 2 Jan, 2024Introducing the SlashID Remix SDK: Authentication made easy
We’re excited to announce first-party Remix support in SlashID with @slashid/remix. We've borrowed the power of our React SDK and aligned it with Remix's unique design patterns.
The Remix SDK makes authentication for Remix easy and seamless.


Security
/ 27 Nov, 2023Firebase Authentication and Google Identity Platform User Enumeration Vulnerability
Firebase Authentication and Google Identity Platform are the two Google products that offer identity management.
Both products suffer from a vulnerability that allows an attacker to enumerate users on an application powered by Firebase Authentication or Google Identity Platform.
In this article, we’ll show how this vulnerability can be used and what the impact is.



New Feature
/ 27 Oct, 2023GDPR Compliance: Consent Management
Effortless GDPR compliance out of the box. Notify users about your intent to use cookies and request their consent.

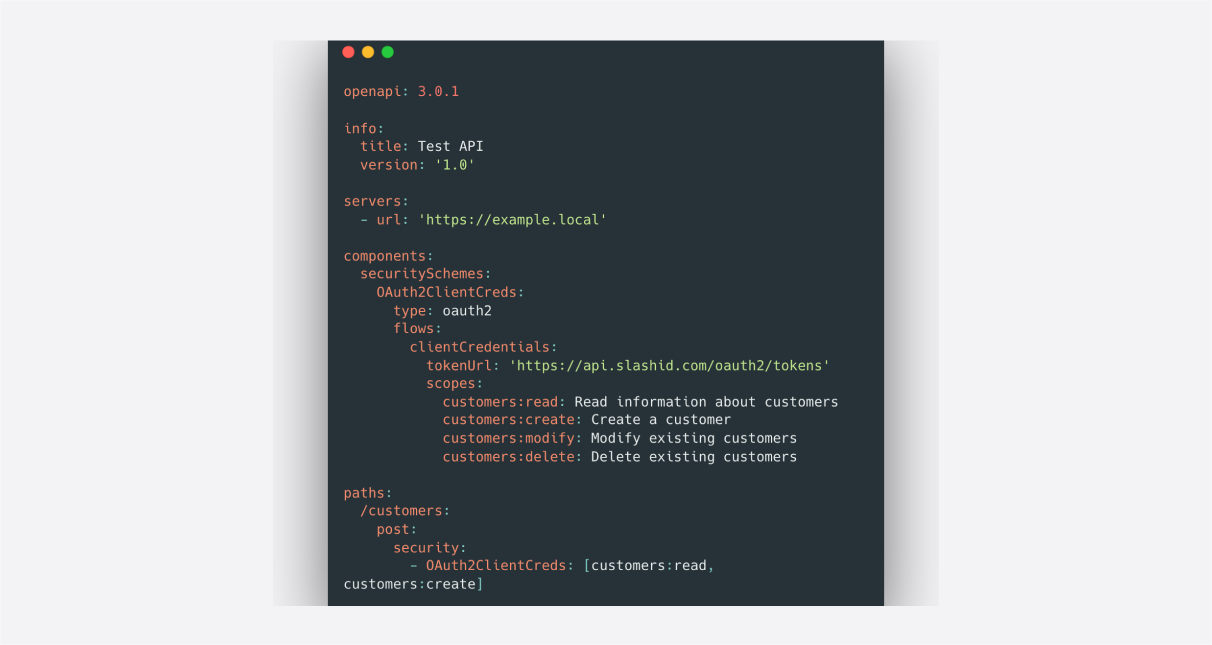
New Feature
/ 23 Oct, 2023OAuth 2.0 Fine-Grained API Authorization with Gate and OpenAPI
Protect your API against unauthorized access without changing your application.
Our newest Gate plugin automatically enforces OpenAPI security checks, so you can implement fine-grained access control for your APIs and workloads without writing any extra code.


Tutorial
/ 16 Oct, 2023Rate Limiting for Large-scale, Distributed Applications and APIs Using GCRA
Rate limiting is a key defense against bots and threats for APIs and backends. Traditional IP-based rate limiting techniques are insufficient today because they can be easily bypassed.
In this article, we discuss the state of the art when it comes to rate limiting and how we have implemented a modern, distributed, identity-based rate limiting plugin for Gate.


Tutorial
/ 10 Oct, 2023Context-aware authentication: fight identity fraud and qualify your users
Knowing your users is becoming increasingly important. Whether you're a B2B PLG business trying to convert leads or a fintech business fending off attacks, it's essential to have more context about who is accessing your platform and to customize your behavior accordingly.
In this article, we show how you can leverage SlashID's webhooks to enrich the authentication context, customize the user journey, block malicious users.

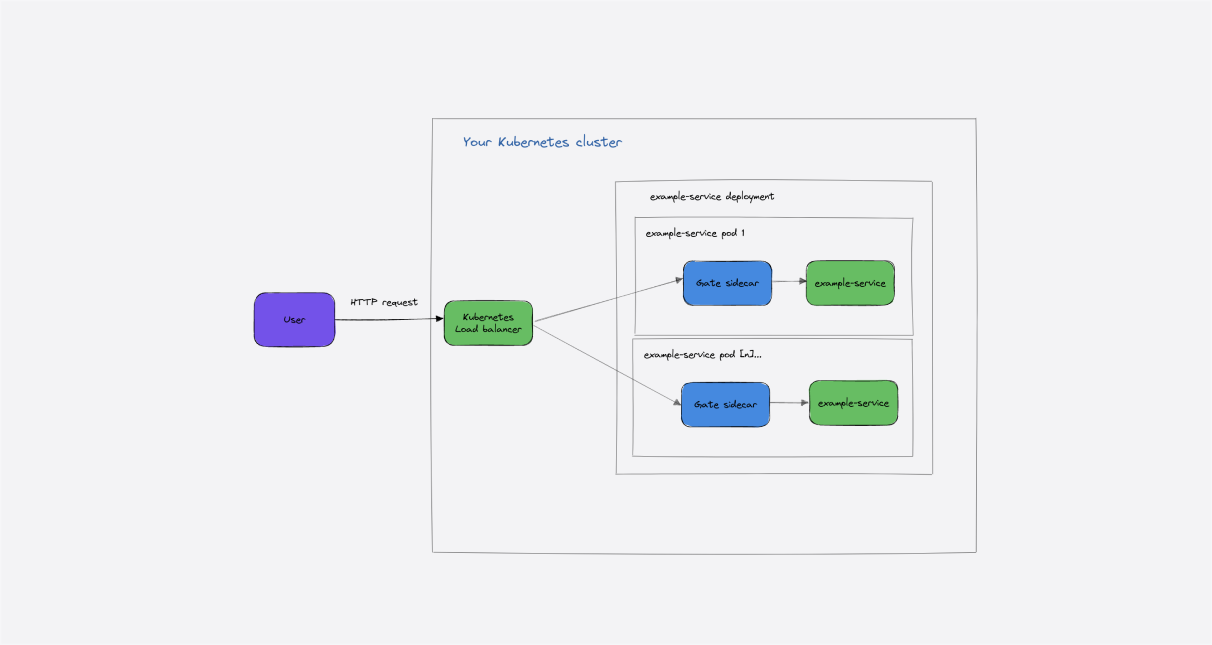
Deep Dives
/ 28 Sep, 2023Backend Authentication and Authorization Patterns: Benefits and Pitfalls of Each
Identity in distributed applications is hard. In large and complex environments with multiple services, a number of patterns have emerged to authenticate and authorize traffic.
In this article, we’ll discuss the most common ones, how to implement them, and their pros and cons.


